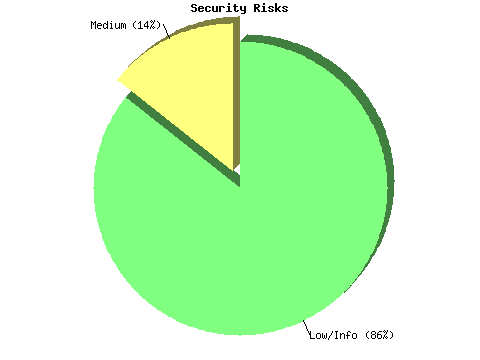

Information found on port general/tcp
The remote host is up
Nessus ID : 10180
Information found on port general/tcp
Using the remote HTTP banner, it is possible to guess that the
Linux distribution installed on the remote host is :
- Debian 4.0 (etch)
Nessus ID : 18261
Information found on port general/tcp
Remote operating system : Linux Kernel 2.6 on Debian 4.0 (etch)
Confidence Level : 95
Method : SSH
Not all fingerprints could give a match - please email the following to os-signatures@nessus.org :
HTTP:!:Server: Apache/2.2.3 (Debian) PHP/5.2.0-8+etch7
SNMP:!:P-660HW-T3
SSH:SSH-2.0-OpenSSH_4.3p2 Debian-9
The remote host is running Linux Kernel 2.6 on Debian 4.0 (etch)
Nessus ID : 11936
Information found on port general/tcp
85.207.205.222 resolves as daemoncze.ath.cx.
Nessus ID : 12053
Information found on port general/tcp
Synopsis :
The remote service implements TCP timestamps.
Description :
The remote host implements TCP timestamps, as defined by RFC1323.
A side effect of this feature is that the uptime of the remote
host can be sometimes be computed.
See also :
http://www.ietf.org/rfc/rfc1323.txt
Risk factor :
None
Nessus ID : 25220
Information found on port general/tcp
Information about this scan :
Nessus version : 2.2.8 (Nessus 2.2.10 is available - consider upgrading)
Plugin feed version : 200709271815
Type of plugin feed : Registered (7 days delay)
Scanner IP : 192.168.2.155
Port scanner(s) : nessus_tcp_scanner
Port range : 1-15000
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
Max hosts : 20
Max checks : 4
Scan Start Date : 2007/9/28 4:02
Scan duration : 830 sec
Nessus ID : 19506
Information found on port ssh (22/tcp)
An ssh server is running on this port
Nessus ID : 10330
Information found on port ssh (22/tcp)
Synopsis :
An SSH server is listening on this port.
Description :
It is possible to obtain information about the remote SSH
server by sending an empty authentication request.
Risk factor :
None
Plugin output :
SSH version : SSH-2.0-OpenSSH_4.3p2 Debian-9
SSH supported authentication : publickey,password
Nessus ID : 10267
Information found on port ssh (22/tcp)
Synopsis :
A SSH server is running on the remote host.
Description :
This plugin determines which versions of the SSH protocol
the remote SSH daemon supports.
Risk factor :
None
Plugin output :
The remote SSH daemon supports the following versions of the
SSH protocol :
. 1.99
. 2.0
SSHv2 host key fingerprint : ca:fa:5b:f6:d9:b2:d5:58:4c:4d:0d:81:9c:98:55:69
Nessus ID : 10881
Information found on port smtp (25/tcp)
An SMTP server is running on this port
Here is its banner :
220 webserver.localdomain ESMTP Postfix (Debian/GNU)
Nessus ID : 10330
Information found on port smtp (25/tcp)
Synopsis :
An SMTP server is listening on the remote port.
Description :
The remote host is running a mail (SMTP) server on this port.
Since SMTP servers are the targets of spammers, it is recommended you
disable it if you do not use it.
Solution :
Disable this service if you do not use it, or filter incoming traffic
to this port.
Risk factor :
None
Plugin output :
Remote SMTP server banner :
220 webserver.localdomain ESMTP Postfix (Debian/GNU)
Nessus ID : 10263
Information found on port http (80/tcp)
A web server is running on this port
Nessus ID : 10330
Information found on port http (80/tcp)
Synopsis :
It is possible to enumerate web directories.
Description :
This plugin attempts to determine the presence of various
common dirs on the remote web server.
Risk factor :
None
Plugin output :
The following directories were discovered:
/cgi-bin
While this is not, in and of itself, a bug, you should manually inspect
these directories to ensure that they are in compliance with company
security standards
Other references : OWASP:OWASP-CM-006
Nessus ID : 11032
Information found on port http (80/tcp)
The following CGI have been discovered :
Syntax : cginame (arguments [default value])
. (C=S;O [A] C=N;O [D] C=M;O [A] C=D;O [A] )
Directory index found at /
Nessus ID : 10662
Information found on port http (80/tcp)
Synopsis :
A web server is running on the remote host.
Description :
This plugin attempts to determine the type and the version of
the remote web server.
Risk factor :
None
Plugin output :
The remote web server type is :
Apache/2.2.3 (Debian) PHP/5.2.0-8+etch7
Solution : You can set the directive 'ServerTokens Prod' to limit
the information emanating from the server in its response headers.
Nessus ID : 10107
Information found on port http (80/tcp)
Synopsis :
Debugging functions are enabled on the remote HTTP server.
Description :
The remote webserver supports the TRACE and/or TRACK methods. TRACE and TRACK
are HTTP methods which are used to debug web server connections.
It has been shown that servers supporting this method are subject to
cross-site-scripting attacks, dubbed XST for "Cross-Site-Tracing", when
used in conjunction with various weaknesses in browsers.
An attacker may use this flaw to trick your legitimate web users to give
him their credentials.
Solution :
Disable these methods.
See also :
http://www.kb.cert.org/vuls/id/867593
Risk factor :
Low / CVSS Base Score : 2
(AV:R/AC:L/Au:NR/C:P/A:N/I:N/B:N)
Solution :
Add the following lines for each virtual host in your configuration file :
RewriteEngine on
RewriteCond %{REQUEST_METHOD} ^(TRACE|TRACK)
RewriteRule .* - [F]
Plugin output :
The server response from a TRACE request is :
TRACE /Nessus1318281960.html HTTP/1.1
Connection: Keep-Alive
Host: daemoncze.ath.cx
Pragma: no-cache
User-Agent: Mozilla/4.75 [en] (X11, U; Nessus)
Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, image/png, */*
Accept-Language: en
Accept-Charset: iso-8859-1,*,utf-8
CVE : CVE-2004-2320
BID : 9506, 9561, 11604
Other references : OSVDB:877, OSVDB:3726
Nessus ID : 11213
Information found on port http (80/tcp)
Synopsis :
Some information about the remote HTTP configuration can be extracted.
Description :
This test gives some information about the remote HTTP protocol - the
version used, whether HTTP Keep-Alive and HTTP pipelining are enabled,
etc...
This test is informational only and does not denote any security
problem
Solution :
None.
Risk factor :
None
Plugin output :
Protocol version : HTTP/1.1
SSL : no
Pipelining : yes
Keep-Alive : yes
Options allowed : GET,HEAD,POST,OPTIONS,TRACE
Headers :
Date: Fri, 28 Sep 2007 00:02:20 GMT
Server: Apache/2.2.3 (Debian) PHP/5.2.0-8+etch7
Content-Length: 737
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=windows-1250
Nessus ID : 24260
Warning found on port snmp (161/udp)
Synopsis :
The System Information of the remote host can be obtained via SNMP.
Description :
It is possible to obtain the system information about the remote
host by sending SNMP requests with the OID 1.3.6.1.2.1.1.1.
An attacker may use this information to gain more knowledge about
the target host.
Solution :
Disable the SNMP service on the remote host if you do not use it,
or filter incoming UDP packets going to this port.
Risk factor :
Medium / CVSS Base Score : 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Plugin output :
System information :
sysDescr : P-660HW-T3
sysObjectID : 1.3.6.1.4.1.890.1.2.6.56
sysUptime : 2d 7h 32m 42s
sysContact : Jan Cernohorsky
sysName : P660HW-T3
sysLocation : Praha
sysServices : 14
Nessus ID : 10800
Warning found on port snmp (161/udp)
Synopsis :
The community name of the remote SNMP server can be guessed.
Description :
It is possible to obtain the default community names of the remote
SNMP server.
An attacker may use this information to gain more knowledge about
the remote host, or to change the configuration of the remote
system (if the default community allow such modifications).
Solution :
Disable the SNMP service on the remote host if you do not use it,
filter incoming UDP packets going to this port, or change the
default community string.
Risk factor :
Medium / CVSS Base Score : 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Plugin output :
The remote SNMP server replies to the following default community
strings :
public
CVE : CVE-1999-0517, CVE-1999-0186, CVE-1999-0254, CVE-1999-0516
BID : 11237, 10576, 177, 2112, 6825, 7081, 7212, 7317, 9681, 986
Other references : IAVA:2001-B-0001
Nessus ID : 10264
Warning found on port snmp (161/udp)
Synopsis :
The list of network interfaces cards of the remote host can be obtained via
SNMP.
Description :
It is possible to obtain the list of the network interfaces installed
on the remote host by sending SNMP requests with the OID 1.3.6.1.2.1.2.1.0
An attacker may use this information to gain more knowledge about
the target host.
Solution :
Disable the SNMP service on the remote host if you do not use it,
or filter incoming UDP packets going to this port.
Risk factor :
Medium / CVSS Base Score : 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Plugin output :
Interface 1 information :
ifIndex : 1
ifDescr : enet0
ifPhysAddress : 001349ed572b
Interface 2 information :
ifIndex : 2
ifDescr : enet1
ifPhysAddress : 001349ed572b
Interface 3 information :
ifIndex : 3
ifDescr : pppoe
ifPhysAddress :
Nessus ID : 10551
Information found on port general/udp
For your information, here is the traceroute from 192.168.2.155 to 85.207.205.222 :
192.168.2.155
192.168.2.1
89.177.117.1
86.49.54.1
194.50.100.206
84.244.127.246
85.207.205.222
Nessus ID : 10287